This post is a continuation of my previous post where I explained my learnings on Day 1 of the KCD.
Talk 4- Cloud Native Anti-Patterns Weakening Your Security by Rotem Refael
In this presentation, Rotem talked about the challenges when you adopt cloud-native solutions. OSS enables faster innovations, but along with that comes a lot of security issues and challenges.

She further talked about "Why security matters in Cloud Native Env.

A few examples which lead to security vulnerabilities are
Spaghetti Code
Code that will be useful later
Relying on one familiar tool
Manual Deployment
Over relying on DevOps tooling
Ignoring Metrics
The first thing we should do to avoid vulnerability is to Update the SW first. We usually use dependencies without realizing that they may have some vulnerabilities. Companies or maintainers do security assessments of those packages from time to time and release a secure/updated version. We should always consider updating those dependencies in our software lifecycle

NoOps
The shift to DevOps and NoOps can lead to security being overlooked if it is not integrated into the development and deployment processes.
Mitigation: Incorporate security into the DevOps lifecycle (DevSecOps) provide security training for developers, and use automated security testing tools.
In certain companies, the responsibility will move to platform Engineering team.
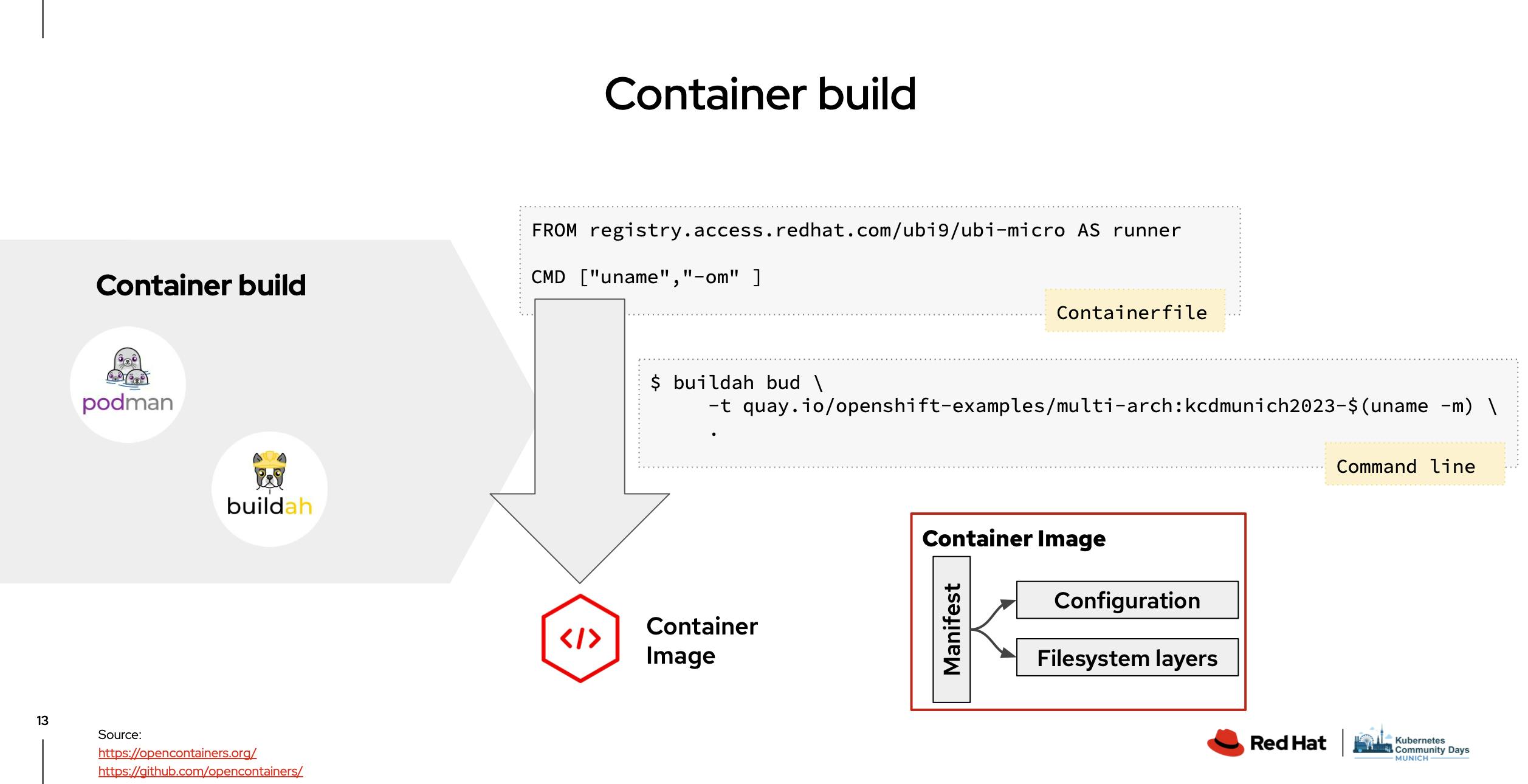
Talk 5- Demystifying Container Images: Understanding Multi-Architecture Manifests, IDs and Digests by Robert Bohne
This talk was very interesting one, where Robert showed how we can create a container image that will be compatible with both ARM64 and AMD64 architecture using buildah tool.
Though things are very common, there is always something new.
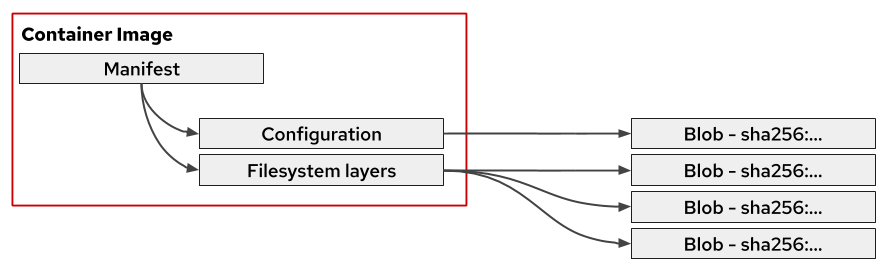
In the container registry, the configuration and filesystem layers are stored as a blob.
To visualize this a bit:
multi-arch images, which are just another manifest
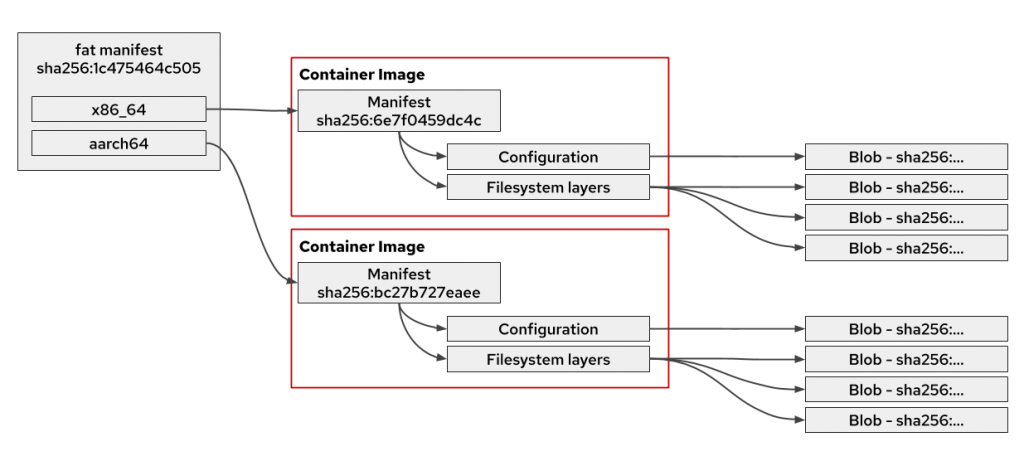
there is a very well document written on this.
another useful link:
https://github.com/openshift-examples/multi-arch/blob/main/README.md
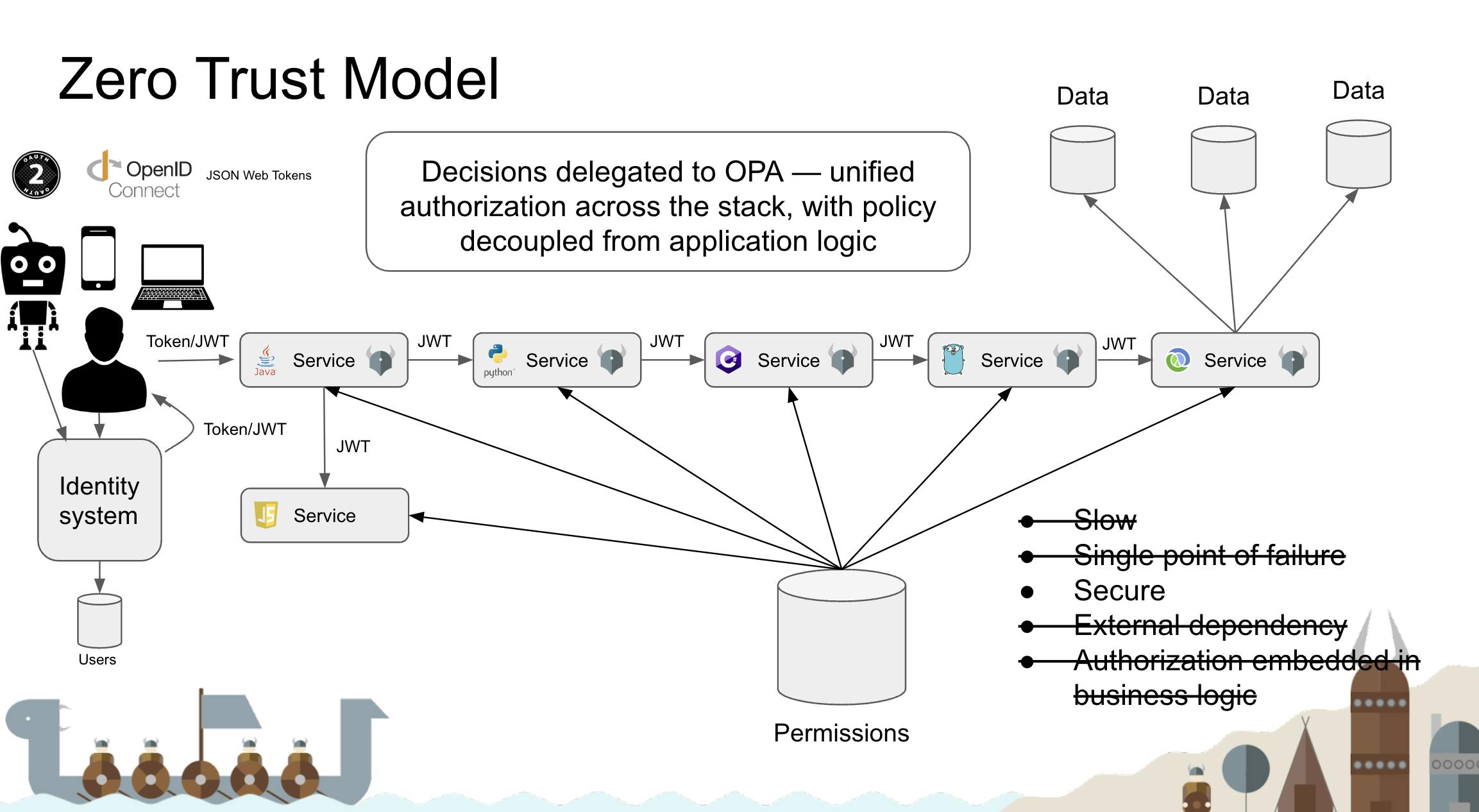
Talk 6- Distributed authorization with Open Policy Agent by Anders Eknert
in this talk, Anders started with the basic issue of a monolith application identity management and showed us how gradually maintaining security and identity became more complex as software started moving toward microservice architecture.
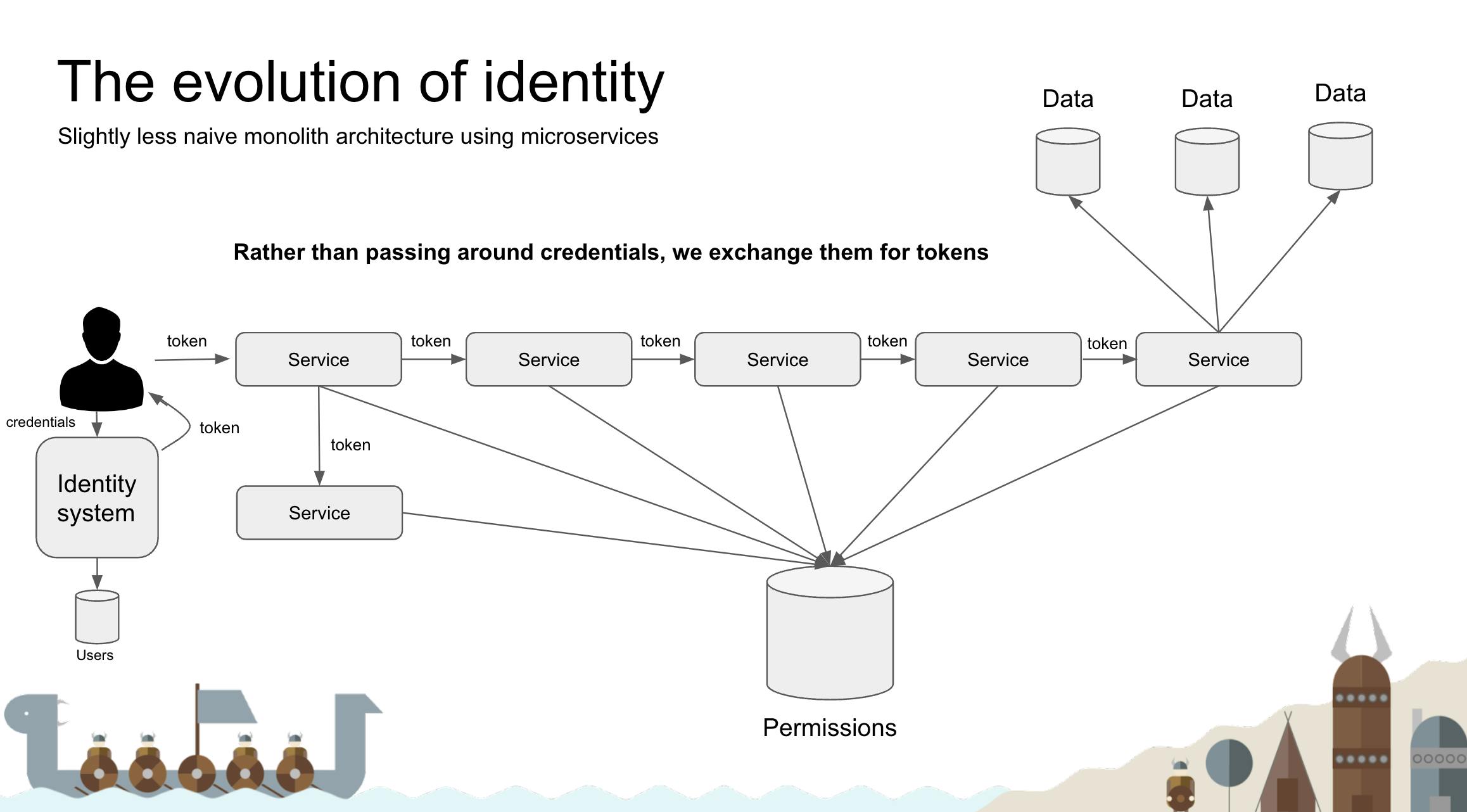
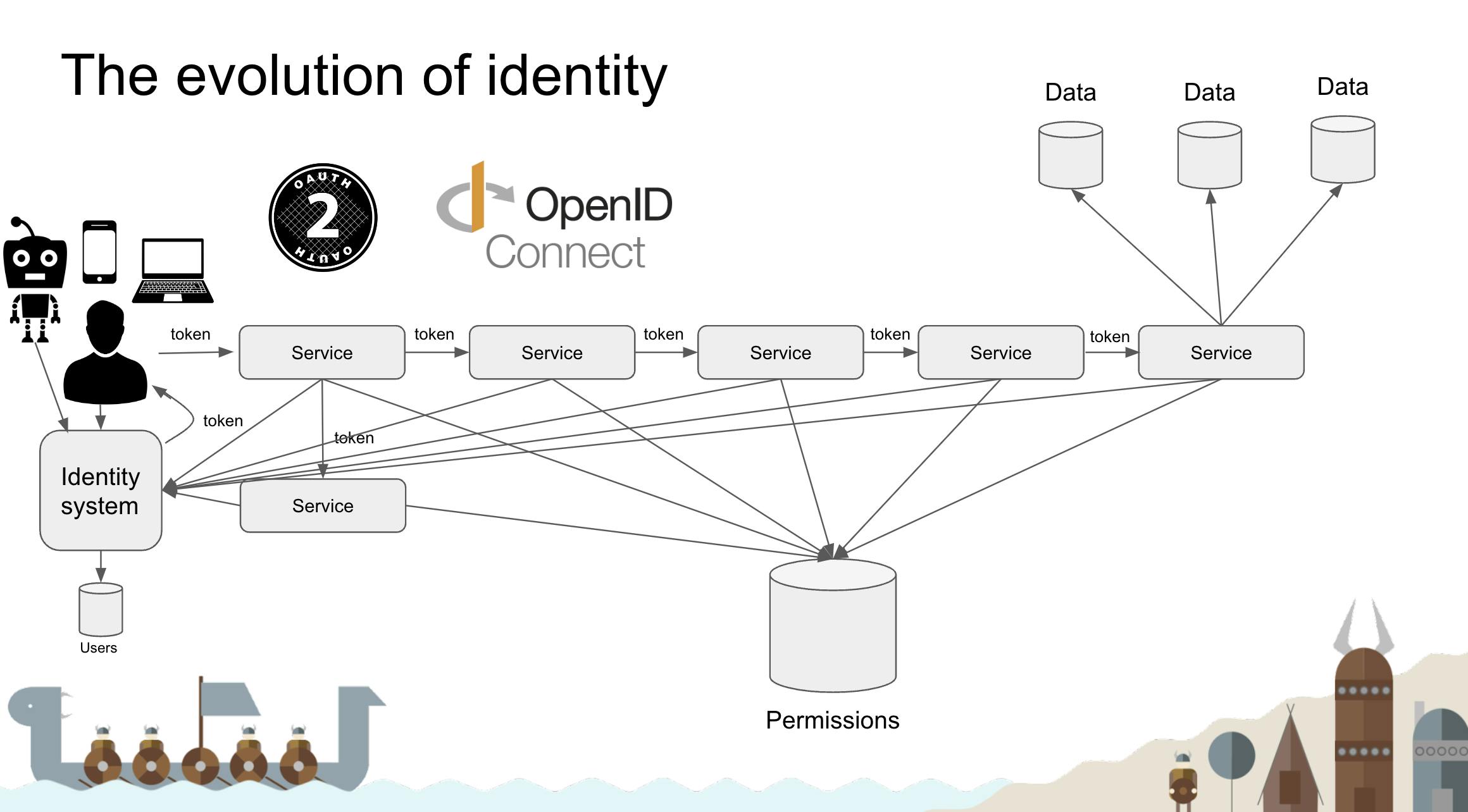
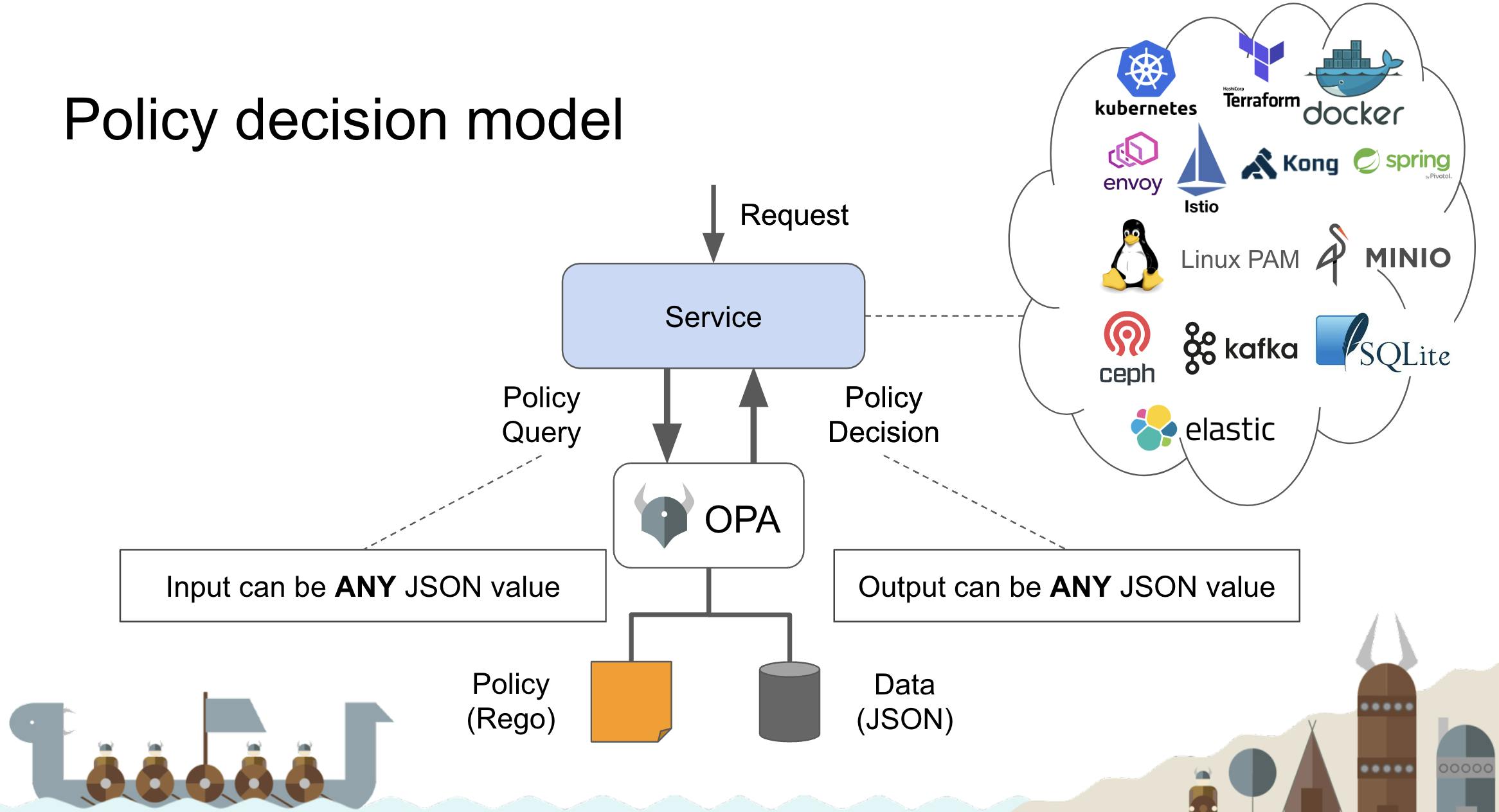
The Open Policy Agent (OPA, pronounced “oh-pa”) is an open source, general-purpose policy engine that unifies policy enforcement across the stack. OPA provides a high-level declarative language that lets you specify policy as code and simple APIs to offload policy decision-making from your software. You can use OPA to enforce policies in microservices, Kubernetes, CI/CD pipelines, API gateways, and more.
OPA was originally created by Styra and is proud to be a graduated project in the Cloud Native Computing Foundation (CNCF) landscape. For details read the CNCF announcement.
in terms of Kelsey Hightower:
Useful links:
https://communityinviter.com/apps/openpolicyagent/signup
Here I will end PART 2 of my blog. in PART 3, I will talk about
Cilium
Blue turns green! Approaches and technologies for sustainable K8s clusters. etc
Thank You :)